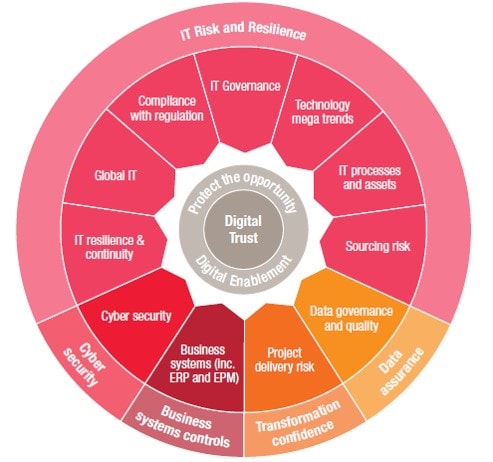
As organizations pivot toward becoming digital more data is generated exponentially and shared among organizations business partners and customers.
Business security solutions pwc.
Learn more about our capabilities and how pwc and aws have helped their clients.
Manager business security solutions at pwc madrid madrid spain 500 connections.
The cybersecurity department of necsia it consulting was acquired by cyberproof ust global which allowed me to finish the internship there.
Not your father s pwc.
Business owned and standardized access management processes reduced business time spent on access reviews by 60 greater transparency into who has what access reduced complexity of roles leads to sustainable lower cost sap security processes significant increase in business user support capabilities sap security solutions 5.
Our solutions help you replace your existing security information and event management siem solution or implement a new cyber operations.
Pwc has teamed with microsoft to develop managed cyber operations solutions that rapidly integrate azure sentinel driven threat detection and response tdr capabilities into your existing it estate.
Seek opportunities to learn about other cultures and other parts of the business across the network of pwc firms.
De 2020 2 meses.
Uphold the firm s code of ethics and business conduct.
De 2020 actualidad 2 meses.
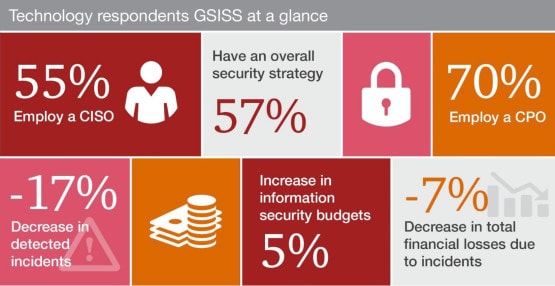
Digitization also exposes companies to new vulnerabilities making effective cyber security more important than ever as every organization is at risk.
Explore pwc s services and solutions powered by amazon web services aws.
De 2019 ene.
Analytics and monitoring.
Business security solutions consultant pwc.
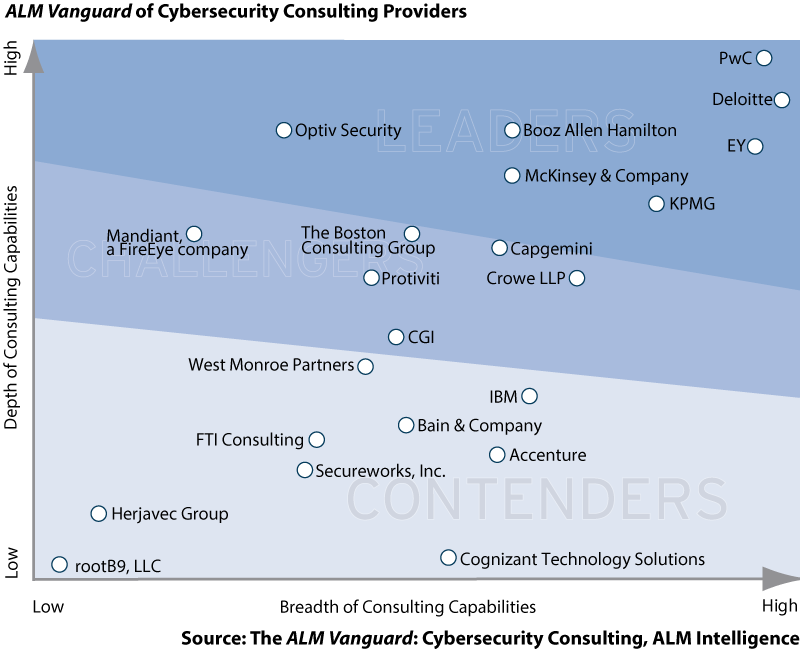
Pwc put into place by strategic foresight or happenstance the building blocks needed to evolve from a traditional consultancy into a business solutions provider in its own terms tbr special report pwc products.
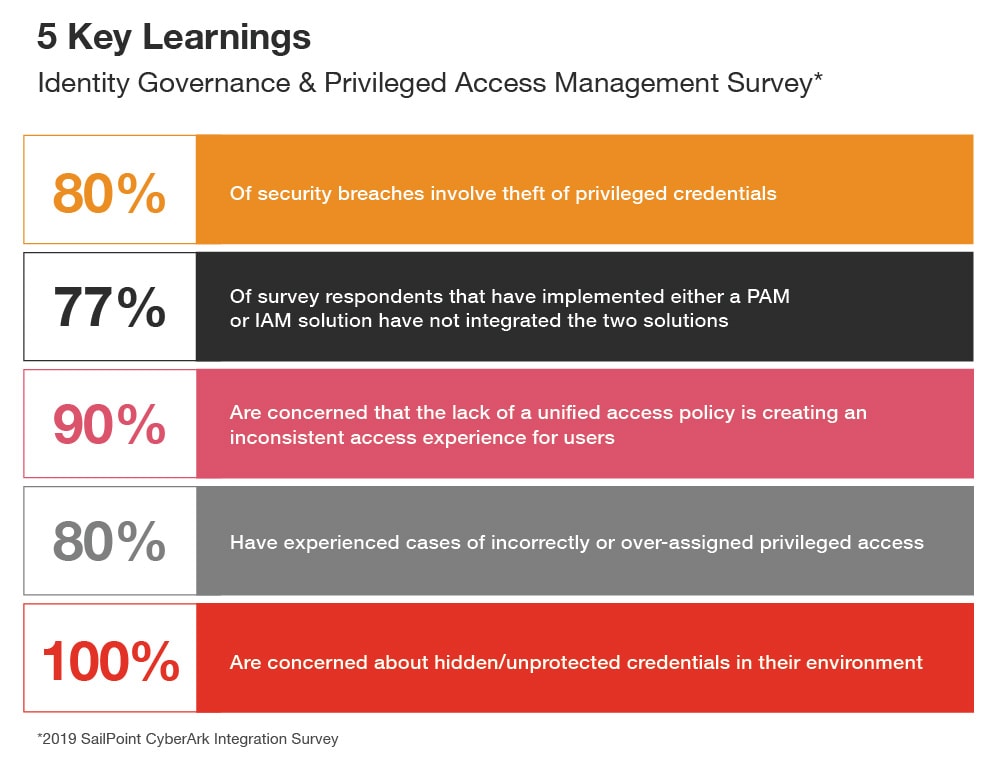
Identity and access management.
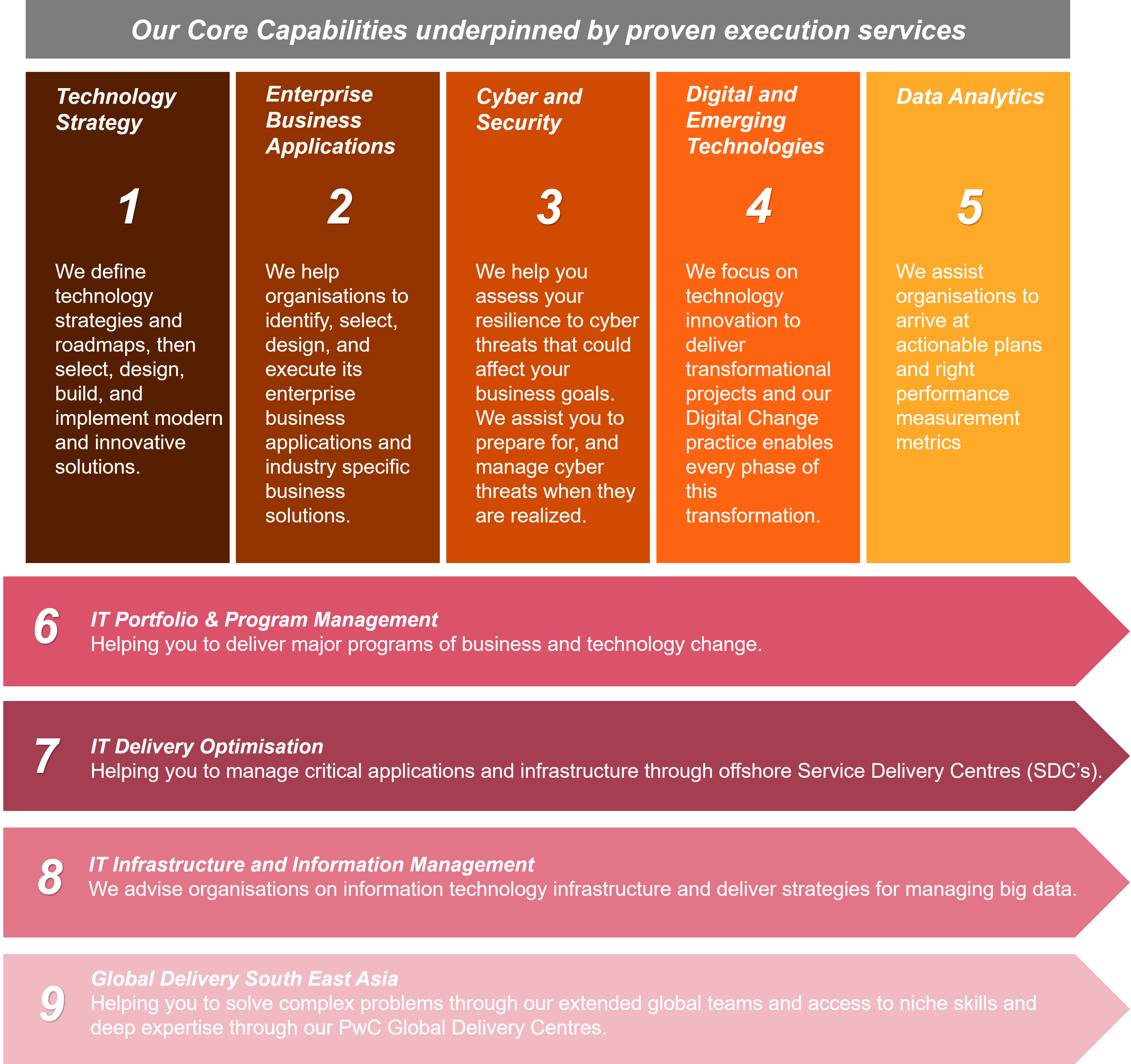
Additionally we also help clients define business driven enterprise security architecture create sustainable solutions to provide foundational capabilities and operational discipline and maintain agility in the event of business technology changes and protect the value of our client s information.